| Getting your Trinity Audio player ready… |
Nowadays, email fraud isn’t “just out there” — it’s flourishing. Big time happy with generative AI, cybercriminals are automating deception at scale, daily dropping hyper-realistic phishing emails and even deepfake audio and video, so unprepared eyes cannot tell what’s real and what’s fake.
A survey from the Global Cybersecurity Outlook 2026 report makes the scale of the threat unmistakably clear: 73% of respondents were personally impacted by cyber-enabled fraud in 2025, and 62% of those cases stemmed from phishing and other email-based attacks.
- What Is a Real Email?
- What Is a Fake Email?
- 🤨Why Does this Scream “FAKE”?
- How to Know If an Email Is Fake?
- How to Spot a Phishing Email?
- How to Verify If an Email Address Is Real or Fake?
- Inspect the Sender (Properly)
- Don’t Trust Whatever Domains
- Hover Before You Click
- Run Emails Through Verification Tools
- Is It Illegal To Make a Fake Email?
- How To Prevent Phishing Emails?
- Key Takeaways
That’s exactly why this post will show you how to tell if an email is fake, how to spot a fishing email, and protect your sender reputation, sensitive data, and peace of mind — whether at work or in your personal inbox.
What Is a Real Email?
A real email is a credible message in your inbox from a verified person or organization. It is backed by proven records, such as familiar domains, accurate contact details, and a clear reason to get in touch.
Whenever you’re suspicious and wondering whether this is a real email, look for the elements above.
Take a look at the following example of a real email:
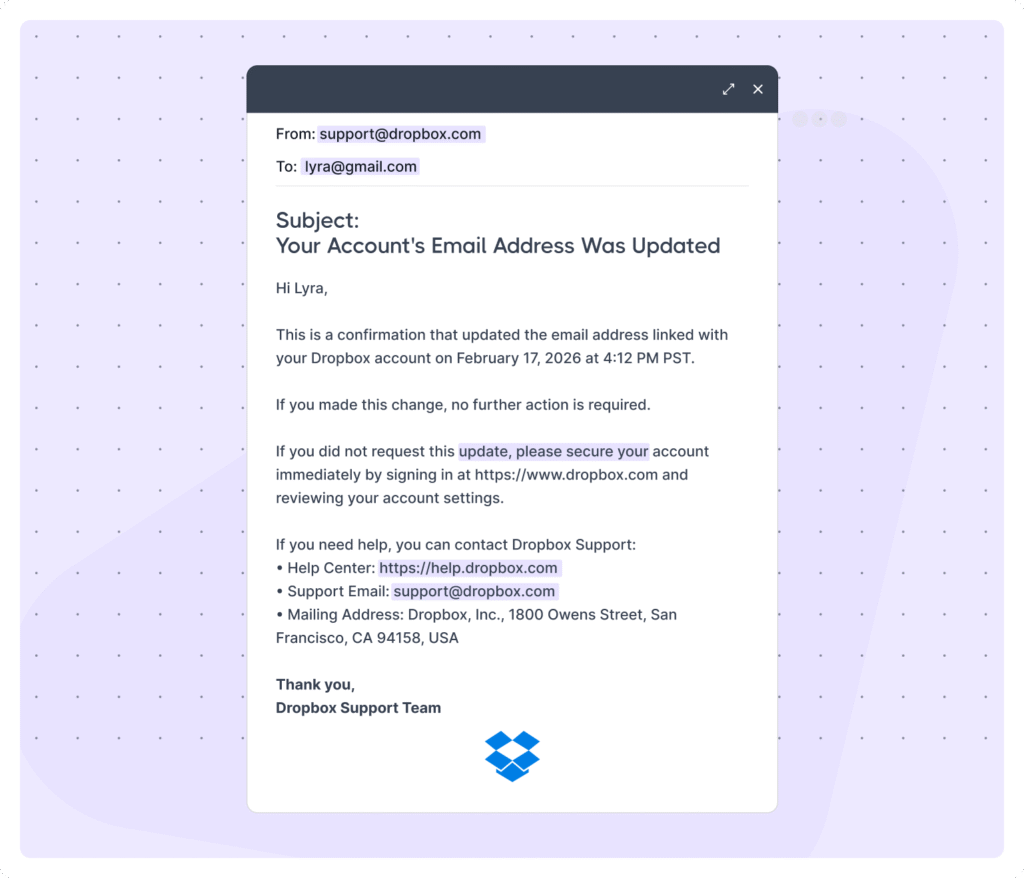
What Is a Fake Email?
A fake email is a deceptive inbox message sent to commit fraud or to mislead the recipient into taking unsafe actions, such as disclosing private information. The sender often pretends to be a trusted person or a real organization.
Common signs of a fake message include a mismatched or odd email address, a suspicious link, inaccurate contact details, and emotional pressure.
Fake emails are often designed like this:
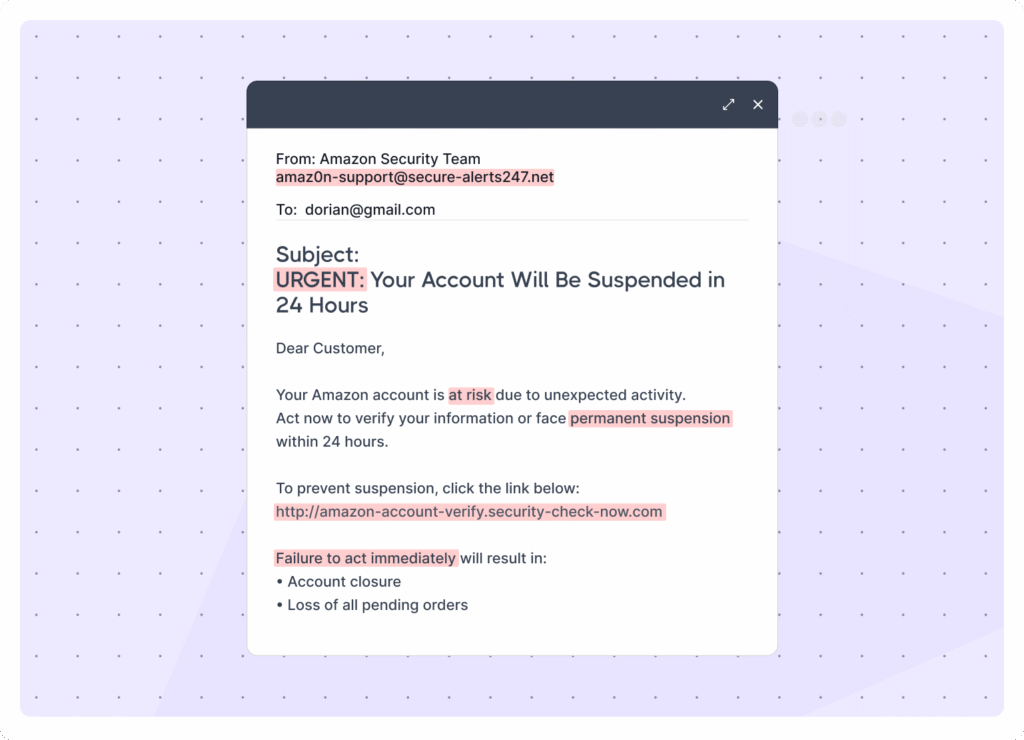
🤨Why Does this Scream “FAKE”?
- “Amazon” is spelled with a zero instead of an “o” (Amaz0n) — a common trick.
- The domain is secure-alerts247.net, not an official amazon.com domain.
- The link is not to Amazon.com, but to a completely different domain — security-check-now.com.
- The email subject is completely intended to create panic and pressure.
- The email says “Dear Customer” instead of your real name, while real Amazon will always use your full account name.
- The email ends suddenly, with no signature, phone number, footer, or other details.
💡Pro-tip! These red flags signal a fake email and they point to phishing, a serious scam designed to steal your passwords, financial information, or internal company data.
How to Know If an Email Is Fake?
When you look closely, you’ll notice that fake emails have patterns that repeat every single time. And here’s another thing: the red flags are as wide-ranging as they are complex, but you’ll notice right away the most common ones.
Here’s how to tell if an email is fake:
1. Weird Sender’s Address
First things first, inspect the sender’s address — specifically the actual domain. Before clicking any links or replying, it’s smart to ask: Is this a real email address?
At first glance, the display name might look legit — “Apple Security,” for example.
But when you click and see apple-support-alerts@outlook.com or security@appple.com, that public email domain or extra letter is a clear sign it is a fake email.
So, make it a habit always to check the domain hiding next to the sender’s name.
💡Pro-tip! Scrutinize the full email address. Minor typos, extra characters, or unfamiliar domains should trigger suspicion.
2. Faulty Formatting or Language
Many fake emails feel stale, often including:
- Grammar mistakes that make you cringe.
- Woolly wording that’s off.
- Misspellings that slip through.
- Inconsistent fonts or broken layouts.
For most people, this is the easiest tell.
💡Pro-tip! Renowned brands and legitimate organizations don’t send sloppy comms unless it’s a targeted spear-phishing attempt.
3. No Real Contact Details
Genuine emails always come with a complete signature — a credible address, a valid phone number, and a clear link to an official support page. If you notice any of these details missing, it’s a good sign that the email might not be genuine.
4. Woolly Attachments
It’s really important to avoid opening email attachments that you weren’t expecting or that seem a bit off. These files might contain dangerous content, such as executable files (.exe, .scr) or compressed archives (.zip, .rar), which can install malware or viruses on your device.

How to Spot a Phishing Email?
Different from regular fake emails, fishing emails are more malignant and calculated — they’re designed to look credible, evoke urgency, and push you into acting fast without thinking. In many instances, they work since they cause the victim’s emotions to override logic.
Learn how they use psychological pressure to make you act before it’s too late (or so they say).
1. Imposed Immediacy and Fear
This is a common approach threat actors adopt — they run carefully crafted campaigns to scare you or force you to act quickly.
👉Examples
- “Your package is on hold due to a payment issue. Respond now to prevent cancellation.”
- “Final notice: Legal action will begin if payment is not received today.”
- “Unusual login detected — failure to confirm now may result in data loss.”
2. Too-Good-to-Be-True Promises
Did you receive an email promising huge rewards with little or no work? Take a beat before clicking!
👉Examples
- “Congratulations. You just won $100,000!
- “Claim your prize now!”
- “Grab your exclusive reward now!”
💡Pro-tip! If you think about it, why would a Fortune 500 company randomly gift you cash? If anything, the promise of free money should make you more suspicious, not less.
3. Fake Login or Payment Links
Emails with bogus login pages or payment links are intended to capture your personal or company information.
At first glance, the message may look real. But when you examine closely, mismatched URLs, HTTP instead of HTTPS, or weird domains make the bad intentions obvious.
No matter how real the branding looks, the link does the talking.
4. Requests for Private Data
Legit companies don’t ask for your password or card details via email. Period.
This one might seem so obvious, yet people fall for it every day. If you find such a message in your inbox, call it a day on that email…delete immediately!
5. Stolen or Copycat Branding
Phishers pull together logos, colors, and templates from trusted brands to create convincing fakes.
You might be surprised to learn how pixel-perfect some clones are — so much so that at first glance, it might look like your bank.
Keep an eye out for:
- Color inconsistencies;
- Blurry or stretched logos;
- Wrong fonts or spacing.
💡Pro-tip! While real brands obsess over detail, fakes cut corners.
How to Verify If an Email Address Is Real or Fake?
Follow several steps to check is this a real email address:
Inspect the Sender (Properly)
Not sure about that message you got?
Here’s how to verify email ID is fake or real: click the sender’s name to reveal the full address instead of going along with the display name.
The truth is, attackers spoof “John Smith at Microsoft” while the real address reads john.smith@micro.soft-login.com.
With that in mind, always verify the domain matches the official website. This could be the single step that saves your account.
Don’t Trust Whatever Domains
Domain health is a great scanner for fraudulent campaigns, as most use newly registered or blacklisted domains.
Remember to check these out:
- Domain spelling (obvious but critical);
- Domain age (new = suspicious);
- Whether the site actually exists;
- If it uses HTTPS (a secure version of a website’s address to protect your data).
In this regard, a brand-new domain claiming to be a 20-year-old bank is a massive red flag.
💡Pro-tip! Free domain lookup tools let you check registration dates and domain health for free.
Hover Before You Click
Before clicking, hover over any link to preview its real address and verify if it is legit.
👉Example
Email says: netflix.com
Hover shows: netflix-login-secure.xyz
That mismatch is a clear stop sign. After all, the URL never lies.
Also, watch for shortened URLs (bit.ly, tinyurl) as they’re significant caution indicators.
💡Pro-tip! Every professional should know how to check if an email is real or fake using the hover-before-clicking method to guard sensitive information.
Run Emails Through Verification Tools
Manual checks are good, but that’s a lot of work at scale.
For businesses, Email Verification Tools is the best alternative — they allow you to check sender domains, confirm mailbox existence, and flag disposable or role-based addresses on the go.
Automation can quickly recognize risky emails before they affect your campaigns, besides protecting your domain reputation, minimizing hard bounces, and guaranteeing your messages reach only verified, engaged recipients.
💡Pro-tip! Consider Dripify, an email verification tool that helps protect you from fake contacts across both LinkedIn and email.
See Dripify in action:
👉Instant Email Search On LinkedIn & Beyond
Grab leads and contact info straight from LinkedIn search results, Sales Navigator, Recruiter, “My Network”, or upload a CSV.
Even if a prospect hasn’t shared a valid email on LinkedIn, Dripify’s LinkedIn Email Finder will find their pre-verified professional addresses elsewhere without endless Googling.
This feature is available next to each lead’s name in your list.
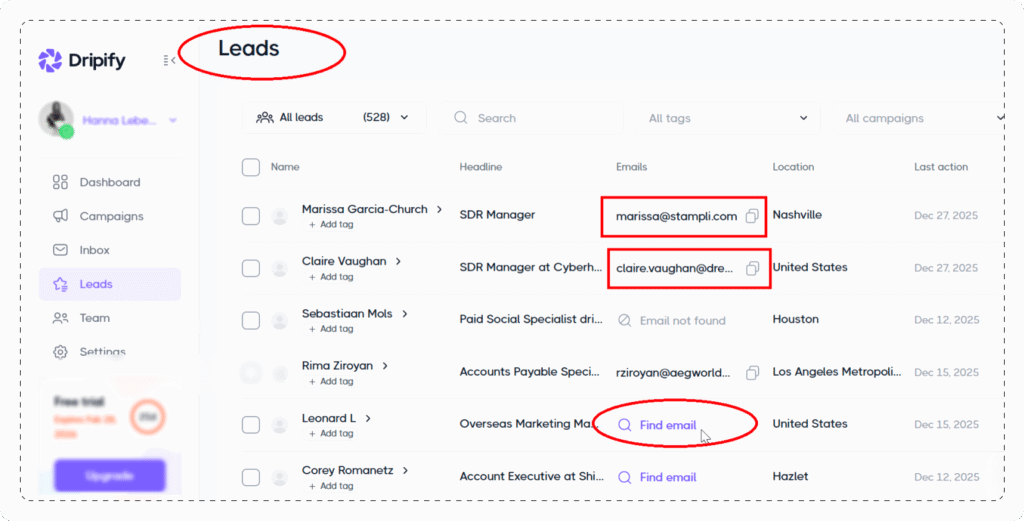
You see, it is super easy to toggle from LinkedIn outreach to email without interrupting your workflow.
👉Email Verification With 98% Accuracy
Dripify’s built-in Email Verifier helps you determine whether an email address is valid, active, and safe to use — so you can avoid stale, fake, or risky contacts.
Backed by advanced validation algorithms, it:
- Checks domain health;
- Catches syntax and formatting errors;
- Confirms mailbox existence at the server level.
👉Email Search & Verification — Without Leaving Your Sequence
Dripify leverages a custom Drip Campaigns sequence builder that automates LinkedIn outreach with human-like behavior for every action, from connection requests to profile views and likes to InMails — all timed naturally.
Its major feature is the ability to combine LinkedIn and email touchpoints within a single sequence.
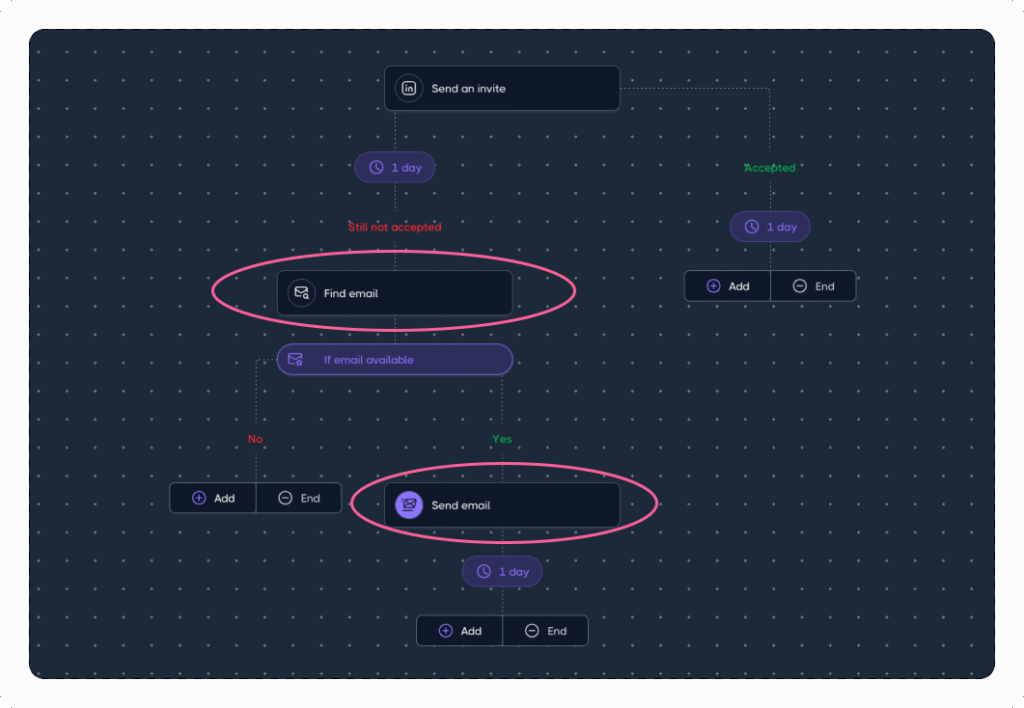
Simply add the “Find Email” step to your outreach campaign, and the tool will automatically source pre-verified email addresses and embed them directly into your sequence.
With “Send Email,” your pitch goes straight to a real, verified address — making bounces a thing of the past.
Is It Illegal To Make a Fake Email?
Yes, it is illegal to create a fake email with the intent to commit fraud, falsely represent oneself as another person or organization, or steal data.
It leads to serious legal consequences, including criminal charges and civil liability.
How To Prevent Phishing Emails?
You get to build a defense-in-depth strategy to protect yourself from phishing attacks.
Start with these:
- Add a second lock: enable 2FA: No matter if hackers steal your password, double-authentication can stop a breach.
- Use a password manager — no reuse, no risk: A password manager generates and stores secure login info every single time, keeping one hack from affecting your entire digital life.
- Use spam protection: Enable anti-spam filters both at your mailbox and gateway levels.
- Look for false urgency, fear, and prizes: Being aware of these standard manipulation techniques can keep you safe.
- Stay on top of scam tricks: Follow reliable cybersecurity news and guides to see how threats are changing.
Key Takeaways
- 👉A real email comes from a verified domain with transparent, consistent details.
- 👉Fake emails often have unusual addresses, messy formats, or random files.
- 👉Hover before clicking, always.
- 👉At all times, verify domains and sender addresses.
- 👉Use email verification tools to automate safety and protect deliverability.
- 👉Dripify’s Email Verifier and LinkedIn Email Finder help you reclaim confidence in every outreach.
- 👉2FA, password managers, and awareness dramatically reduce phishing risk.
Recommended For You
LinkedIn Call to Action for Lead Generation
LinkedIn has always been at the forefront of introducing new and exciting features to help businesses make the best use…
![Email Outreach Tracking [Tips, Tricks and Tools]](https://dripify.com/wp-content/uploads/2025/02/11-7.png)
Email Outreach Tracking [Tips, Tricks and Tools]
Email outreach is one of the most effective and affordable marketing tools available to reach your target customers. As a…
![Create a Prospecting Plan [+8 Prospecting Methods]](https://dripify.com/wp-content/uploads/2025/02/11.png)
Create a Prospecting Plan [+8 Prospecting Methods]
No matter your business, you need a steady flow of new prospects for a steady revenue stream. Prospecting is time-intensive…
Try out a smarter way to crush sales
Kickstart your sales outreach campaign today and see your first results in less than 48 hours, while enjoying your free trial
10 people or more? Get a personalized introduction to Dripify